Compare commits
24 Commits
example
...
TouchID_4_
| Author | SHA1 | Date | |
|---|---|---|---|
|
|
b39fa1a99b | ||
|
|
c5b62ada65 | ||
|
|
3d37d0a51f | ||
|
|
a820206a24 | ||
|
|
bc407ca39b | ||
|
|
9786f4a888 | ||
|
|
804b76518e | ||
|
|
91d08cdafc | ||
|
|
7ee2281785 | ||
|
|
288ab96425 | ||
|
|
36e9bf154a | ||
|
|
0b0a3230fa | ||
|
|
5d31b83fae | ||
|
|
c134cd87e2 | ||
|
|
ab4b1fdf5a | ||
|
|
2d5b507a50 | ||
|
|
7800962eb6 | ||
|
|
3ac3e101a3 | ||
|
|
4c31e1815e | ||
|
|
64dafb8d2e | ||
|
|
9086f47456 | ||
|
|
03ab360939 | ||
|
|
3a85efc1e6 | ||
|
|
9555c7820b |
26
CHANGELOG.md
Normal file
26
CHANGELOG.md
Normal file
@@ -0,0 +1,26 @@
|
||||
# Change Log
|
||||
|
||||
## v1.9.1
|
||||
* Fixed: is_authenticated #13
|
||||
* Fixed: is_anonymous #6
|
||||
|
||||
thanks to @d3cline,
|
||||
|
||||
## v1.7
|
||||
* Better Error Management
|
||||
* Better Token recheck
|
||||
## v 1.6.0
|
||||
* Fixed some issues for django>= 2.0
|
||||
* Added example app.
|
||||
|
||||
## v.1.5.0
|
||||
* Added id the key used to validate to the session dictionary as 'id'
|
||||
## v1.4.0
|
||||
* Updated to FIDO == 0.7
|
||||
|
||||
## v1.3.0
|
||||
* Updated to FIDO2 == 0.6
|
||||
* Windows Hello is now supported.
|
||||
|
||||
## v1.2.0
|
||||
* Added: MFA_HIDE_DISABLE setting option to disable users from deactivating their keys.
|
||||
14
README.md
14
README.md
@@ -8,10 +8,10 @@ Web Authencation API (WebAuthn) is state-of-the art techology that is expected t
|
||||
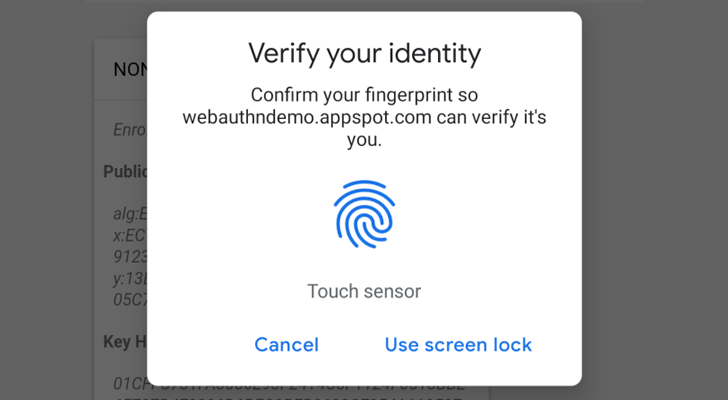
|
||||
|
||||
For FIDO2, the following are supported
|
||||
* **security keys** (Firefox 60+, Chrome 67+, Edge 18+),
|
||||
* **security keys** (Firefox 60+, Chrome 67+, Edge 18+, Safari 13 on Mac OS, Chrome on Andriod, Safari on iOS 13.3+),
|
||||
* **Windows Hello** (Firefox 67+, Chrome 72+ , Edge) ,
|
||||
* **Apple's Touch ID** (Chrome 70+ on Mac OS X ),
|
||||
* **android-safetynet** (Chrome 70+)
|
||||
* **android-safetynet** (Chrome 70+, Firefox 68+)
|
||||
* **NFC devices using PCSC** (Not Tested, but as supported in fido2)
|
||||
|
||||
In English :), It allows you to verify the user by security keys on PC, Laptops or Mobiles, Windows Hello (Fingerprint, PIN) on Windows 10 Build 1903+ (May 2019 Update) Touch ID on Macbooks (Chrome) and Fingerprint/Face/Iris/PIN on Andriod Phones.
|
||||
@@ -53,6 +53,7 @@ Depends on
|
||||
MFA_RECHECK_MAX=30 # Maximum in seconds
|
||||
MFA_QUICKLOGIN=True # Allow quick login for returning users by provide only their 2FA
|
||||
MFA_HIDE_DISABLE=('FIDO2',) # Can the user disable his key (Added in 1.2.0).
|
||||
MFA_OWNED_BY_ENTERPRISE = FALSE # Who ownes security keys
|
||||
|
||||
TOKEN_ISSUER_NAME="PROJECT_NAME" #TOTP Issuer name
|
||||
|
||||
@@ -68,8 +69,9 @@ Depends on
|
||||
* Trusted_Devices
|
||||
* Email
|
||||
|
||||
**Note**: Starting version 1.1, ~~FIDO_LOGIN_URL~~ isn't required for FIDO2 anymore.
|
||||
|
||||
**Notes**:
|
||||
* Starting version 1.1, ~~FIDO_LOGIN_URL~~ isn't required for FIDO2 anymore.
|
||||
* Starting version 1.7.0, Key owners can be specified.
|
||||
1. Break your login function
|
||||
|
||||
Usually your login function will check for username and password, log the user in if the username and password are correct and create the user session, to support mfa, this has to change
|
||||
@@ -150,3 +152,7 @@ function some_func() {
|
||||
}
|
||||
|
||||
````
|
||||
|
||||
# Contributors
|
||||
* [mahmoodnasr](https://github.com/mahmoodnasr)
|
||||
* [d3cline](https://github.com/d3cline)
|
||||
|
||||
@@ -127,8 +127,8 @@ LOGIN_URL="/auth/login"
|
||||
EMAIL_FROM='Test App'
|
||||
EMAIL_HOST="smtp.gmail.com"
|
||||
EMAIL_PORT=587
|
||||
EMAIL_HOST_USER="mkalioby@gmail.com"
|
||||
EMAIL_HOST_PASSWORD='wanted85'
|
||||
EMAIL_HOST_USER=""
|
||||
EMAIL_HOST_PASSWORD=''
|
||||
EMAIL_USE_TLS=True
|
||||
|
||||
|
||||
|
||||
@@ -1,13 +0,0 @@
|
||||
# Change Log
|
||||
|
||||
## v.1.5.0
|
||||
* Added id the key used to validate to the session dictionary as 'id'
|
||||
## v1.4.0
|
||||
* Updated to FIDO == 0.7
|
||||
|
||||
## v1.3.0
|
||||
* Updated to FIDO2 == 0.6
|
||||
* Windows Hello is now supported.
|
||||
|
||||
## v1.2.0
|
||||
* Added: MFA_HIDE_DISABLE setting option to disable users from deactivating their keys.
|
||||
45
mfa/FIDO2.py
45
mfa/FIDO2.py
@@ -12,14 +12,15 @@ from django.conf import settings
|
||||
from .models import *
|
||||
from fido2.utils import websafe_decode,websafe_encode
|
||||
from fido2.ctap2 import AttestedCredentialData
|
||||
from .views import login
|
||||
from .views import login,reset_cookie
|
||||
import datetime
|
||||
from django.utils import timezone
|
||||
|
||||
def recheck(request):
|
||||
context = csrf(request)
|
||||
context["mode"]="recheck"
|
||||
return request("FIDO2/recheck.html", context)
|
||||
request.session["mfa_recheck"]=True
|
||||
return render(request,"FIDO2/recheck.html", context)
|
||||
|
||||
|
||||
def getServer():
|
||||
@@ -52,13 +53,16 @@ def complete_reg(request):
|
||||
uk=User_Keys()
|
||||
uk.username = request.user.username
|
||||
uk.properties = {"device":encoded,"type":att_obj.fmt,}
|
||||
uk.owned_by_enterprise=getattr(settings,"MFA_OWNED_BY_ENTERPRISE",False)
|
||||
uk.key_type = "FIDO2"
|
||||
uk.save()
|
||||
return HttpResponse(simplejson.dumps({'status': 'OK'}))
|
||||
except Exception as exp:
|
||||
try:
|
||||
from raven.contrib.django.raven_compat.models import client
|
||||
import traceback
|
||||
client.captureException()
|
||||
except:
|
||||
pass
|
||||
return HttpResponse(simplejson.dumps({'status': 'ERR',"message":"Error on server, please try again later"}))
|
||||
def start(request):
|
||||
context = csrf(request)
|
||||
@@ -83,6 +87,7 @@ def authenticate_begin(request):
|
||||
|
||||
@csrf_exempt
|
||||
def authenticate_complete(request):
|
||||
try:
|
||||
credentials = []
|
||||
username=request.session.get("base_username",request.user.username)
|
||||
server=getServer()
|
||||
@@ -92,7 +97,7 @@ def authenticate_complete(request):
|
||||
client_data = ClientData(data['clientDataJSON'])
|
||||
auth_data = AuthenticatorData(data['authenticatorData'])
|
||||
signature = data['signature']
|
||||
|
||||
try:
|
||||
cred = server.authenticate_complete(
|
||||
request.session.pop('fido_state'),
|
||||
credentials,
|
||||
@@ -101,8 +106,27 @@ def authenticate_complete(request):
|
||||
auth_data,
|
||||
signature
|
||||
)
|
||||
keys = User_Keys.objects.filter(username=username, key_type="FIDO2",enabled=1)
|
||||
except ValueError:
|
||||
return HttpResponse(simplejson.dumps({'status': "ERR", "message": "Wrong challenge received, make sure that this is your security and try again."}),
|
||||
content_type = "application/json")
|
||||
except Exception as excep:
|
||||
try:
|
||||
from raven.contrib.django.raven_compat.models import client
|
||||
client.captureException()
|
||||
except:
|
||||
pass
|
||||
return HttpResponse(simplejson.dumps({'status': "ERR",
|
||||
"message": excep.message}),
|
||||
content_type = "application/json")
|
||||
|
||||
if request.session.get("mfa_recheck",False):
|
||||
import time
|
||||
request.session["mfa"]["rechecked_at"]=time.time()
|
||||
return HttpResponse(simplejson.dumps({'status': "OK"}),
|
||||
content_type="application/json")
|
||||
else:
|
||||
import random
|
||||
keys = User_Keys.objects.filter(username=username, key_type="FIDO2", enabled=1)
|
||||
for k in keys:
|
||||
if AttestedCredentialData(websafe_decode(k.properties["device"])).credential_id == cred.credential_id:
|
||||
k.last_used = timezone.now()
|
||||
@@ -112,6 +136,15 @@ def authenticate_complete(request):
|
||||
mfa["next_check"] = int((datetime.datetime.now()+ datetime.timedelta(
|
||||
seconds=random.randint(settings.MFA_RECHECK_MIN, settings.MFA_RECHECK_MAX))).strftime("%s"))
|
||||
request.session["mfa"] = mfa
|
||||
try:
|
||||
authenticated=request.user.is_authenticated
|
||||
except:
|
||||
authenticated = request.user.is_authenticated()
|
||||
if not authenticated:
|
||||
res=login(request)
|
||||
if not "location" in res: return reset_cookie(request)
|
||||
return HttpResponse(simplejson.dumps({'status':"OK","redirect":res["location"]}),content_type="application/json")
|
||||
return HttpResponse(simplejson.dumps({'status': "err"}),content_type="application/json")
|
||||
return HttpResponse(simplejson.dumps({'status': "OK"}),
|
||||
content_type = "application/json")
|
||||
except Exception as exp:
|
||||
return HttpResponse(simplejson.dumps({'status': "ERR","message":exp.message}),content_type="application/json")
|
||||
|
||||
@@ -12,6 +12,7 @@ from django.conf import settings
|
||||
from django.http import HttpResponse
|
||||
from .models import *
|
||||
from .views import login
|
||||
import datetime
|
||||
from django.utils import timezone
|
||||
|
||||
def recheck(request):
|
||||
@@ -26,6 +27,8 @@ def recheck(request):
|
||||
def process_recheck(request):
|
||||
x=validate(request,request.user.username)
|
||||
if x==True:
|
||||
import time
|
||||
request.session["mfa"]["rechecked_at"] = time.time()
|
||||
return HttpResponse(simplejson.dumps({"recheck":True}),content_type="application/json")
|
||||
return x
|
||||
|
||||
@@ -89,6 +92,7 @@ def bind(request):
|
||||
User_Keys.objects.filter(username=request.user.username,key_type="U2F").delete()
|
||||
uk = User_Keys()
|
||||
uk.username = request.user.username
|
||||
uk.owned_by_enterprise = getattr(settings, "MFA_OWNED_BY_ENTERPRISE", False)
|
||||
uk.properties = {"device":simplejson.loads(device.json),"cert":cert_hash}
|
||||
uk.key_type = "U2F"
|
||||
uk.save()
|
||||
|
||||
@@ -1 +1 @@
|
||||
__version__="1.5.0"
|
||||
__version__="1.6.0"
|
||||
|
||||
20
mfa/migrations/0009_user_keys_owned_by_enterprise.py
Normal file
20
mfa/migrations/0009_user_keys_owned_by_enterprise.py
Normal file
@@ -0,0 +1,20 @@
|
||||
# -*- coding: utf-8 -*-
|
||||
from __future__ import unicode_literals
|
||||
|
||||
from django.db import models, migrations
|
||||
from django.conf import settings
|
||||
|
||||
class Migration(migrations.Migration):
|
||||
|
||||
dependencies = [
|
||||
('mfa', '0008_user_keys_last_used'),
|
||||
]
|
||||
|
||||
operations = [
|
||||
migrations.AddField(
|
||||
model_name='user_keys',
|
||||
name='owned_by_enterprise',
|
||||
field=models.NullBooleanField(default=None),
|
||||
),
|
||||
migrations.RunSQL("update mfa_user_keys set owned_by_enterprise = %s where key_type='FIDO2'"%(True if getattr(settings,"MFA_OWNED_BY_ENTERPRISE",False) else False ))
|
||||
]
|
||||
@@ -13,6 +13,8 @@ class User_Keys(models.Model):
|
||||
enabled=models.BooleanField(default=True)
|
||||
expires=models.DateTimeField(null=True,default=None,blank=True)
|
||||
last_used=models.DateTimeField(null=True,default=None,blank=True)
|
||||
owned_by_enterprise=models.NullBooleanField(default=None,null=True,blank=True)
|
||||
|
||||
def save(self, force_insert=False, force_update=False, using=None, update_fields=None):
|
||||
if self.key_type == "Trusted Device" and self.properties.get("signature","") == "":
|
||||
self.properties["signature"]= jwt.encode({"username": self.username, "key": self.properties["key"]}, settings.SECRET_KEY)
|
||||
|
||||
9
mfa/static/mfa/js/ua-parser.min.js
vendored
Normal file
9
mfa/static/mfa/js/ua-parser.min.js
vendored
Normal file
File diff suppressed because one or more lines are too long
@@ -2,6 +2,7 @@
|
||||
{% load static %}
|
||||
{% block head %}
|
||||
<script type="application/javascript" src="{% static 'mfa/js/cbor.js'%}"></script>
|
||||
<script type="application/javascript" src="{% static 'mfa/js/ua-parser.min.js'%}"></script>
|
||||
<script type="application/javascript">
|
||||
function begin_reg(){
|
||||
fetch('{% url 'fido2_begin_reg' %}',{}).then(function(response) {
|
||||
@@ -40,7 +41,17 @@
|
||||
$("#res").html("<div class='alert alert-danger'>Registeration Failed as " +reason +", <a href='javascript:void(0)' onclick='begin_reg()'> try again </a> or <a href='{% url 'mfa_home' %}'> Go to Security Home</a></div>")
|
||||
})
|
||||
}
|
||||
$(document).ready(setTimeout(begin_reg,500))
|
||||
$(document).ready(function (){
|
||||
ua=new UAParser()
|
||||
if (ua.getBrowser().name == "Safari")
|
||||
{
|
||||
$("#res").html("<button class='btn btn-primary' onclick='begin_reg()'>Start...</button>")
|
||||
}
|
||||
else
|
||||
{
|
||||
setTimeout(begin_reg, 500)
|
||||
}
|
||||
})
|
||||
</script>
|
||||
|
||||
{% endblock %}
|
||||
@@ -56,7 +67,7 @@
|
||||
|
||||
|
||||
<div class="row alert alert-pr" id="res">
|
||||
<p style="color: green">Your broswer should ask you to confirm you indentity.</p>
|
||||
<p style="color: green">Your browser should ask you to confirm you identity.</p>
|
||||
|
||||
</div>
|
||||
</div>
|
||||
|
||||
@@ -1,6 +1,4 @@
|
||||
{% extends "mfa_auth_base.html" %}
|
||||
{% block content %}
|
||||
<br/>
|
||||
<br/>
|
||||
{% include 'FIDO2/recheck.html' with mode='auth' %}
|
||||
{% endblock %}
|
||||
@@ -1,5 +1,6 @@
|
||||
{% load static %}
|
||||
<script type="application/javascript" src="{% static 'mfa/js/cbor.js' %}"></script>
|
||||
<script type="application/javascript" src="{% static 'mfa/js/us-parser.min.js' %}"></script>
|
||||
<div class="row">
|
||||
|
||||
<div class="col-sm-10 col-sm-offset-1 col-xs-12 col-md-10 col-md-offset-1 col-lg-8 col-lg-offset-2">
|
||||
@@ -17,11 +18,14 @@
|
||||
<br/>
|
||||
|
||||
{% endif %}
|
||||
<div id="res">
|
||||
<p style="color: green">please press the button on your security key to prove it is you.</p>
|
||||
</div>
|
||||
<div id="msgdiv"></div>
|
||||
{% if mode == "auth" %}
|
||||
<form id="u2f_login" action="{% url 'fido2_complete_auth' %}" method="post" enctype="multipart/form-data">
|
||||
{% elif mode == "recheck" %}
|
||||
<form id="u2f_login" action="{% url 'u2f_recheck' %}" method="post">
|
||||
<form id="u2f_login" action="{% url 'fido2_recheck' %}" method="post" enctype="multipart/form-data">
|
||||
{% endif %}
|
||||
{% csrf_token %}
|
||||
<input type="hidden" name="response" id="response" value=""/>
|
||||
@@ -71,6 +75,8 @@
|
||||
}).then(function (response) {if (response.ok) return res = response.json()}).then(function (res) {
|
||||
if (res.status=="OK")
|
||||
{
|
||||
$("#msgdiv").addClass("alert alert-success").removeClass("alert-danger")
|
||||
$("#msgdiv").html("Verified....please wait")
|
||||
{% if mode == "auth" %}
|
||||
window.location.href=res.redirect;
|
||||
{% elif mode == "recheck" %}
|
||||
@@ -78,10 +84,13 @@
|
||||
{% endif %}
|
||||
}
|
||||
else {
|
||||
$("#msgdiv").addClass("alert alert-danger").removeClass("alert-success")
|
||||
$("#msgdiv").html("Verification Failed as " + res.message + ", <a href='javascript:void(0)' onclick='authen())'> try again</a> or <a href='javascript:void(0)' onclick='history.back()'> Go Back</a>")
|
||||
|
||||
{% if mode == "auth" %}
|
||||
alert("Error occured, please try again")
|
||||
login()
|
||||
|
||||
{% elif mode == "recheck" %}
|
||||
|
||||
mfa_failed_function();
|
||||
{% endif %}
|
||||
}
|
||||
@@ -95,6 +104,10 @@
|
||||
$("#main_paragraph").addClass("alert alert-danger")
|
||||
$("#main_paragraph").html("FIDO2 must work under secure context")
|
||||
} else {
|
||||
ua=UAParser()
|
||||
if (ua.getBrowser().name == "Safari")
|
||||
$("#res").html("<button class='btn btn-success' onclick='authen()'>Authenticate...</button>")
|
||||
else
|
||||
authen()
|
||||
}
|
||||
});
|
||||
|
||||
@@ -20,7 +20,7 @@
|
||||
$("#modal-footer").prepend("<button id='actionBtn' class='btn btn-danger' onclick='confirmDel("+id+")'>Confirm Deletion</button>")
|
||||
$("#popUpModal").modal()
|
||||
}
|
||||
{% if not HIDE_DISABLE %}
|
||||
|
||||
function toggleKey(id) {
|
||||
$.ajax({
|
||||
url:"{% url 'toggle_key' %}?id="+id,
|
||||
@@ -34,7 +34,6 @@
|
||||
}
|
||||
})
|
||||
}
|
||||
{% endif %}
|
||||
</script>
|
||||
<link href="{% static 'mfa/css/bootstrap-toggle.min.css' %}" rel="stylesheet">
|
||||
<script src="{% static 'mfa/js/bootstrap-toggle.min.js'%}"></script>
|
||||
|
||||
@@ -24,6 +24,8 @@ def recheck(request):
|
||||
context["mode"]="recheck"
|
||||
if request.method == "POST":
|
||||
if verify_login(request,request.user.username, token=request.POST["otp"]):
|
||||
import time
|
||||
request.session["mfa"]["rechecked_at"] = time.time()
|
||||
return HttpResponse(simplejson.dumps({"recheck": True}), content_type="application/json")
|
||||
else:
|
||||
return HttpResponse(simplejson.dumps({"recheck": False}), content_type="application/json")
|
||||
|
||||
@@ -27,10 +27,7 @@ urlpatterns = [
|
||||
url(r'fido2/complete_auth', FIDO2.authenticate_complete, name="fido2_complete_auth"),
|
||||
url(r'fido2/begin_reg', FIDO2.begin_registeration, name="fido2_begin_reg"),
|
||||
url(r'fido2/complete_reg', FIDO2.complete_reg, name="fido2_complete_reg"),
|
||||
url(r'u2f/bind', U2F.bind, name="bind_u2f"),
|
||||
url(r'u2f/auth', U2F.auth, name="u2f_auth"),
|
||||
url(r'u2f/process_recheck', U2F.process_recheck, name="u2f_recheck"),
|
||||
url(r'u2f/verify', U2F.verify, name="u2f_verify"),
|
||||
url(r'fido2/recheck', FIDO2.recheck, name="fido2_recheck"),
|
||||
|
||||
|
||||
url(r'td/$', TrustedDevice.start, name="start_td"),
|
||||
|
||||
14
mfa/views.py
14
mfa/views.py
@@ -1,5 +1,5 @@
|
||||
from django.shortcuts import render
|
||||
#from django.http import HttpResponse,HttpResponseRedirect
|
||||
from django.http import HttpResponse,HttpResponseRedirect
|
||||
from .models import *
|
||||
try:
|
||||
from django.urls import reverse
|
||||
@@ -7,10 +7,12 @@ except:
|
||||
from django.core.urlresolvers import reverse
|
||||
from django.template.context_processors import csrf
|
||||
from django.template.context import RequestContext
|
||||
from django.http import HttpResponseRedirect
|
||||
from django.conf import settings
|
||||
from . import TrustedDevice
|
||||
from django.contrib.auth.decorators import login_required
|
||||
from user_agents import parse
|
||||
|
||||
@login_required
|
||||
def index(request):
|
||||
keys=[]
|
||||
context={"keys":User_Keys.objects.filter(username=request.user.username),"UNALLOWED_AUTHEN_METHODS":settings.MFA_UNALLOWED_METHODS
|
||||
@@ -52,6 +54,8 @@ def login(request):
|
||||
callable_func = __get_callable_function__(settings.MFA_LOGIN_CALLBACK)
|
||||
return callable_func(request,username=request.session["base_username"])
|
||||
|
||||
|
||||
@login_required
|
||||
def delKey(request):
|
||||
key=User_Keys.objects.get(id=request.GET["id"])
|
||||
if key.username == request.user.username:
|
||||
@@ -73,18 +77,20 @@ def __get_callable_function__(func_path):
|
||||
raise Exception("Module does not have requested function")
|
||||
return callable_func
|
||||
|
||||
@login_required
|
||||
def toggleKey(request):
|
||||
id=request.GET["id"]
|
||||
q=User_Keys.objects.filter(username=request.user.username, id=id)
|
||||
if q.count()==1:
|
||||
key=q[0]
|
||||
if not key.key_type in settings.MFA_HIDE_DISABLE:
|
||||
key.enabled=not key.enabled
|
||||
key.save()
|
||||
return HttpResponse("OK")
|
||||
else:
|
||||
return HttpResponse("You can't change this method.")
|
||||
else:
|
||||
return HttpResponse("Error")
|
||||
|
||||
def goto(request,method):
|
||||
return HttpResponseRedirect(reverse(method.lower()+"_auth"))
|
||||
|
||||
|
||||
|
||||
4
setup.py
4
setup.py
@@ -4,7 +4,7 @@ from setuptools import find_packages, setup
|
||||
|
||||
setup(
|
||||
name='django-mfa2',
|
||||
version='1.5.0',
|
||||
version='1.10.0,
|
||||
description='Allows user to add 2FA to their accounts',
|
||||
long_description=open("README.md").read(),
|
||||
long_description_content_type="text/markdown",
|
||||
@@ -24,7 +24,7 @@ setup(
|
||||
'ua-parser',
|
||||
'user-agents',
|
||||
'python-jose',
|
||||
'fido2 == 0.7',
|
||||
'fido2 == 0.9',
|
||||
'jsonLookup'
|
||||
],
|
||||
python_requires=">=2.7, !=3.0.*, !=3.1.*, !=3.2.*, !=3.3.*",
|
||||
|
||||
Reference in New Issue
Block a user