Adding more docs
This commit is contained in:
23
docs/change_login.md
Normal file
23
docs/change_login.md
Normal file
@@ -0,0 +1,23 @@
|
||||
# Change of login function
|
||||
|
||||
## Break your login function
|
||||
|
||||
Usually your login function will check for username and password, log the user in if the username and password are correct and create the user session, to support mfa, this has to change
|
||||
|
||||
* authenticate the user
|
||||
* if username and password are correct , check if the user has mfa or not
|
||||
* if user has mfa then redirect to mfa page
|
||||
* if user doesn't have mfa then call your function to create the user session
|
||||
|
||||
<code>
|
||||
def login(request): # this function handles the login form POST
|
||||
user = auth.authenticate(username=username, password=password)
|
||||
if user is not None: # if the user object exist
|
||||
from mfa.helpers import has_mfa
|
||||
res = has_mfa(username = username,request=request) # has_mfa returns false or HttpResponseRedirect
|
||||
if res:
|
||||
return res
|
||||
return log_user_in(request,username=user.username)
|
||||
#log_user_in is a function that handles creatung user session, it should be in the setting file as MFA_CALLBACK
|
||||
</code>
|
||||
|
||||
36
docs/index.md
Normal file
36
docs/index.md
Normal file
@@ -0,0 +1,36 @@
|
||||
# django-mfa2
|
||||
A Django app that handles MFA, it supports TOTP, U2F, FIDO2 U2F (Web Authn), Email Tokens , and Trusted Devices
|
||||
|
||||
[](https://badge.fury.io/py/django-mfa2)
|
||||
|
||||
Web Authencation API (WebAuthn) is state-of-the art techology that is expected to replace passwords.
|
||||
|
||||
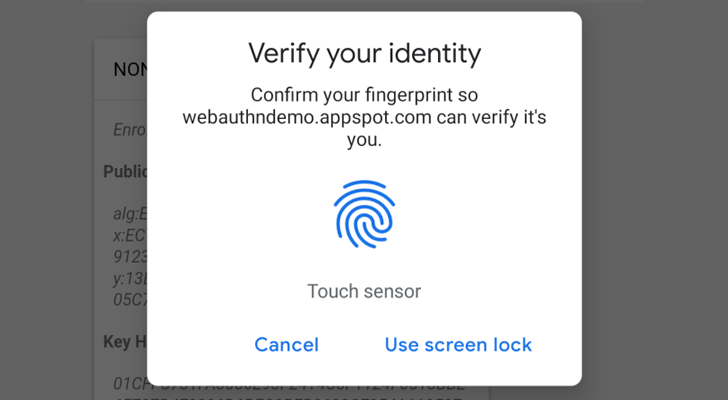
|
||||
|
||||
For FIDO2, both security keys and android-safetynet are supported.
|
||||
|
||||
In English :), It allows you to verify the user by security keys on PC, Laptops and Fingerprint/PIN on Andriod Phones.
|
||||
|
||||
Trusted device is a mode for the user to add a device that doesn't support security keys like iOS and andriod without fingerprints or NFC.
|
||||
|
||||
**Note**: `U2F and FIDO2 can only be served under secure context (https)`
|
||||
|
||||
Package tested with Django 1.8, Django 2.1 on Python 2.7 and Python 3.5+ but it was not checked with any version in between but open for issues.
|
||||
|
||||
Depends on
|
||||
|
||||
* pyotp
|
||||
* python-u2flib-server
|
||||
* ua-parser
|
||||
* user-agents
|
||||
* python-jose
|
||||
* fido2==0.5
|
||||
|
||||
# Example
|
||||
|
||||
For Example, See https://github.com/mkalioby/AutoDeploy/commit/5f1d94b1804e0aa33c79e9e8530ce849d9eb78cc in AutDeploy Project
|
||||
|
||||
# Table of Contents
|
||||
* [Installation](installation.md)
|
||||
* [Change Login Code](change_login.md)
|
||||
|
||||
@@ -36,26 +36,6 @@
|
||||
|
||||
**Note**: Starting version 1.1, ~~FIDO_LOGIN_URL~~ isn't required for FIDO2 anymore.
|
||||
|
||||
1. Break your login function
|
||||
|
||||
Usually your login function will check for username and password, log the user in if the username and password are correct and create the user session, to support mfa, this has to change
|
||||
|
||||
* authenticate the user
|
||||
* if username and password are correct , check if the user has mfa or not
|
||||
* if user has mfa then redirect to mfa page
|
||||
* if user doesn't have mfa then call your function to create the user session
|
||||
|
||||
```python
|
||||
def login(request): # this function handles the login form POST
|
||||
user = auth.authenticate(username=username, password=password)
|
||||
if user is not None: # if the user object exist
|
||||
from mfa.helpers import has_mfa
|
||||
res = has_mfa(username = username,request=request) # has_mfa returns false or HttpResponseRedirect
|
||||
if res:
|
||||
return res
|
||||
return log_user_in(request,username=user.username)
|
||||
#log_user_in is a function that handles creatung user session, it should be in the setting file as MFA_CALLBACK
|
||||
```
|
||||
1. Add mfa to urls.py
|
||||
```python
|
||||
import mfa
|
||||
@@ -73,3 +53,5 @@
|
||||
1. To match the look and feel of your project, MFA includes `base.html` but it needs blocks named `head` & `content` to added its content to it.
|
||||
1. Somewhere in your app, add a link to 'mfa_home'
|
||||
```<li><a href="{% url 'mfa_home' %}">Security</a> </li>```
|
||||
|
||||
Next, you need to [change your login code](change_login.md)
|
||||
|
||||
Reference in New Issue
Block a user